Microsoft Office 365 accounts all are equipped with 2-Factor authentication By default, that service is NOT enabled. The authentication on Office 365 is just password protected. That might be enough security for some businesses, but not for others. 2-Factor Authentication for Office 365 is provided through an Authenticator App that needs to be installed on your smartphone. The 2-Factor authentication assures that you, and only you, are able to login to your email, OneDrive, Sharepoint, and other Microsoft applications.
Two Factor Authentication
Office 365 2-Factor Authentication Security Services
2-Factor Authentication guarantee’s it is you!
With Microsoft 2-Factor, you and only you can open your email and other Office 365 applications and services. This ensures that even if someone has your password, they cannot get to your email, One Drive, SharePoint, and other services without knowing the 2-Factor code that is connected to your account.
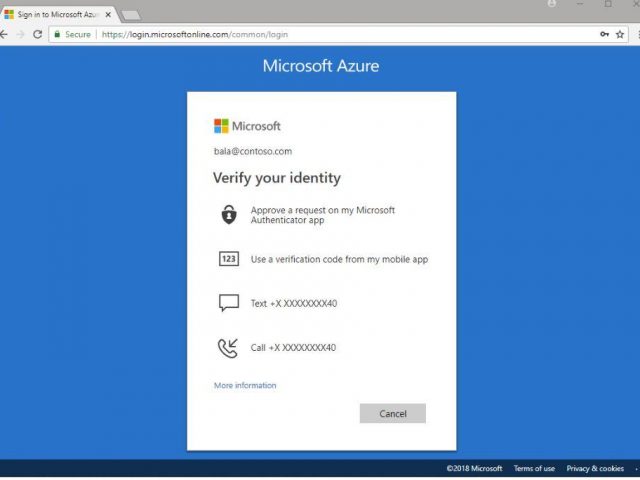
Once 2-Factor is enabled, you then have to add the Microsoft Authenticator to your phone. Anytime there is an attempt to login to your email or Office 365 account, your smartphone will receive a code that you must put in along with your password to get into your account.
What does it look like and will it inconvenience me?
This is the question we get all the time. How much of a bother is it going to be to use 2-Factor? Actually, it is quite easy. Once turned on and enabled, the 2 Factor requires you to login to your email account on the web via http://office.com It has you follow a number of steps including downloading and installing the Microsoft Authenticator on your smartphone. Once setup, that is all
1. Your Outlook will prompt you onetime for your password, and you will have to approve the login via your smartphone ONE TIME.
2. Your email on your phone will also require you to Re-Login. Once you login, again you will have to put in a code. After that one-time re-login and code, you are done!
Essentially, anytime you have a new device, you will have to use the 2-Factor login onetime to connect email and Office 365 applications and services on that device.
2-Factor with Webmail.
This is the easiest implementation of 2-Factor. Each time you login on the web for email, you will have to put in a 2-Factor code. This is the most arduous implementation of 2-Factor. This is why the use of the installed applications is the easiest type of the implementation of 2-Factor for Office 365.
One Drive for Personal and Business, SharePoint 2-Factor.
San Diego Computer Consulting requires that all our clients that use the cloud services by Microsoft have 2-Factor on their accounts. With the trust of putting your personal and company data on the cloud, we insist that you logins are protected to the fullest. We also install backup services for all data on the cloud. However, in today’s environment, we cannot trust Microsoft or anyone else to make sure our data is private and totally secure. With the integration of 2-Factor, we can ensure that you, and only you, have access to your cloud data.
SharePoint security is the MOST Critical with 2-Factor implementations!
SharePoint business data must be secured with 2-Factor – no question about it. Having your business data on the cloud is new. In a file server environment, the data is only local and not necessarily accessible through the internet. With SharePoint, your data is entrusted to the Microsoft Cloud. However, if anyone was to get your login password, that data can be compromised. By enabling 2-Factor services in Office 365, you are ensuring the most protection for that data.
Remote Desktop 2 Factor
**Today’s Ransomware Hackers have found a major flaw in Microsoft Remote Desktop!**
If we could tell you exactly how ransomware hackers have figured out how to encrypt our computers, we would be a different kind of company. We have our guesses, but we are not sure how Microsoft remote desktop services are hacked on computers and servers. What we do know is that we have to protect your data at the front door. The only way we can protect remote desktop services by Microsoft is with 2-Factor authentication. At San Diego Computer Consulting, we use an implementation of DUO 2-Factor. The DUO software system is installed on a Windows Server or Desktop. The service requires that any users that are trying to remote access the system are verified through a 2-factor login.
How do we know it works?
We hate to admit it. But unfortunately, we have had a small number of customers who did contract ransomware viruses. In each case, we had to use the backup system to recover the data that was encrypted. DUO, 2-Factor Authentication services are available on most all remote access systems. Since we have utilized DUO, we have been able to quiet down and defend against most all attacks on our client’s systems. This is especially true for those that have any kind of remote access into their Windows network. Duo ensures that the user, and only the user, who is logging in is that person. Again, this is done with an application on a smartphone.
Additional Defense Systems-The best offense, is a great defense!
San Diego Computer Consulting specializes in IT consulting for many different types of customers in the San Diego area. It is our job to make sure that our clients are computing at the safest levels. Having the best defense systems for computing allows us and our clients to have peace of mind. Along with 2-Factor we strongly suggest the following systems.
Sophos Anti-Virus with Intercept-X
San Diego Computer Consulting installs Sophos anti-virus with Intercept X with its clients. These two products ensure each computer and server is protected from viruses and, more importantly, ransomware. The Intercept X product blocks mass file changes. This service uses artificial intelligence which learns each system and is excellent.
DUO Without 2-Factor
DUO can work with without 2-Factor enabled. It is NOT as secure, but it can be installed on any Windows computer and can be enabled. When you enabled it without 2-Factor it only allows users to pass through who are pre-list in DUO. Therefore, if your login name is on the list, you will be allowed to remote in. If your username is not on the list, then you will be blocked. Of course, a name not to put on the list is: “administrator.” That is a default username on all Windows computers. At San Diego Computer Consulting, we typically do not run DUO in this fashion, unless there is a special circumstance. Nonetheless, it is an option and better than no DUO.
Backup for all critical data systems
Backup is essential to all business computing. Things happen and it is the backup that will save you. We work with a number of different backup systems based on the data and the service that it is on.